Data Integrity can be defined as the extent to which data are complete, intact, consistent, and accurate throughout its lifecycle. Establishing and demonstrating Data Integrity compliance to regulatory agency guidance and industry expectations is required in a GxP regulated environment. The time and effort of ensuring the integrity of your company data can be expensive and overwhelming, but the costs of not doing so can be even more expensive and overwhelming. Regulatory agency and client auditors often cite absent, inadequate, or poorly managed Data Integrity Programs. These observations and warning letters can result in significant consequences for companies, including costly remediation, product recalls, loss of sales, loss of trust and reputational impact.
Data Integrity is not a new expectation from regulatory agencies and industry. The concept of Data Integrity started with the FDA and MHRA predicate rules, progressed further with the issuance of the FDA 21 CFR Part 11 and EudraLex Vol 4 Annex 11 regulations and then more recently, clarified with the Data Integrity guidance from FDA, MHRA and industry organizations such as PIC/S, PDA, WHO and GAMP. There has been a consistent industry focus on accurate GxP data capture and secure data management over several decades.
The FDA expects data to be reliable and accurate because:
- Data Integrity problems undermine the safety, efficacy, and quality of drugs that consumers will take.
- Data Integrity problems break trust, and the FDA relies largely on trusting firms to do the right thing when they are not there.
“In recent years, FDA has increasingly observed CGMP violations involving data integrity during CGMP inspections. This is troubling because ensuring data integrity is an important component of industry’s responsibility to ensure the safety, efficacy, and quality of drugs, and of FDA’s ability to protect the public health. These data integrity related CGMP violations have led to numerous regulatory actions, including warning letters, import alerts, and consent decrees.”
– FDA Data Integrity and Compliance with Drug CGMP Questions and Answers Guidance for Industry (Dec 2018)
The MHRA expects companies to establish confidence in the quality and the integrity of data to ensure patient safety and quality of products and allow reconstruction of activities by:
- Reviewing the effectiveness of internal governance systems to ensure data integrity and traceability as part of self-inspection programs.
- Verifying Data Integrity adequacy when contracting outsourced activities.
- Demonstrating progress towards system upgrades with individual login and audit trails for systems, including industrial automation and control equipment / systems (e.g., programmable logic controller-based systems).
“Where systems do not meet the audit trail and individual user account expectations, demonstrated progress should be available to address these shortcomings. This should either be through add-on software that provides these additional functions or by an upgrade to a compliant system. Where remediation has not been identified or subsequently implemented in a timely manner a deficiency may be cited.“
– MHRA GXP Data Integrity Guidance and Definitions (March 2018)
Consider the following when establishing and executing your company’s Data Integrity Program:
- Corporate and site (where applicable) management must provide the necessary funding and resourcing to establish and maintain an ongoing Data Integrity program.
- Clearly communicated and persuasive Management Team support is essential. Already busy staff will be asked to participate in Data Integrity activities and accommodate potentially significant changes to the established processes they perform. The Management Team must communicate the necessity as well as their commitment and priority for Data Integrity training, assessment, and remediation to staff.
- Regulatory agencies and clients expect that companies performing GxP activities have a Data Integrity Program established with a plan to assess and remediate existing GxP processes and systems, with significant progress made against that plan. Starting in 2015, the MHRA noted that companies should have systems with individual logons and audit trails by the end of 2017 (see MHRA GxP Data Integrity Definitions and Guidance for Industry, March 2015 and July 2016). Companies with a Data Integrity Plan that are tracking progress to that plan have a far better defensive position in an audit than those not having a plan.
- Both existing and new GxP processes and systems should be assessed for Data Integrity compliance gaps. Compliance gaps should be prioritized for remediation for existing GxP processes and systems. Compliance gaps should be remediated prior to implementation of new GxP processes and systems.
- Both enterprise and site based GxP systems should be accessed for compliance gaps. It is recommended that a separate Data Integrity Plan be established for enterprise systems as a whole and then for each individual site to better identify and manage responsibilities, remediation activities and timelines.
- Data Integrity assessments can be performed at the process and system levels. Process level assessments provide the big picture and can identify significant data integrity risks and compliance gaps, such as client data being stored in an unsecured LAN share. System level assessments can identify more discrete data integrity risks and compliance gaps such as raw result data being stored on an unsecured hard drive of an instrument controlling workstation. In both examples, Data Integrity risk is significant as GxP data can be modified or deleted unintentionally or intentionally. A data flow should be established to identify the manual and electronic paths of the data. Both process and system level Data Integrity assessments can add value and should be performed as appropriate for a given data flow.
- Process and system assessments may identify compliance gap trends that have the potential for a common remediation approach. An example is establishing central time source to synchronize the time on servers and workstations to ensure the accurate chronological order of events across multiple systems. Another example is implementing a LIMS, CDS or EDMS to secure data from multiple data inputs or systems.
- Long term remediation actions may be identified, such as having to schedule, fund and implement a system upgrade or replacement. In these situations, consider implementing interim procedural controls while final solutions are being pursued. An example would be establishing an instrument use log while a software upgrade to implement individual logons is scheduled for implementation. Procedural controls are often not as robust as electronic controls, but they demonstrate both a recognition of the compliance gap and an attempt to establish control of it.
- The effort to establish a Data Integrity Program and perform assessment and remediation can be significant. Consideration should be made to backfill key staff to allow them the necessary bandwidth to establish and effectively execute a Data Integrity Plan. When key staff cannot be backfilled or Data Integrity subject matter expertise is not available within your company, consider using consultants to help establish your program, train your staff and progress assessments and remediation activities as needed.
The Structure of a Data Integrity Program
The following diagram presents an overall structure for the definition, execution, and related processes for a Data Integrity program:
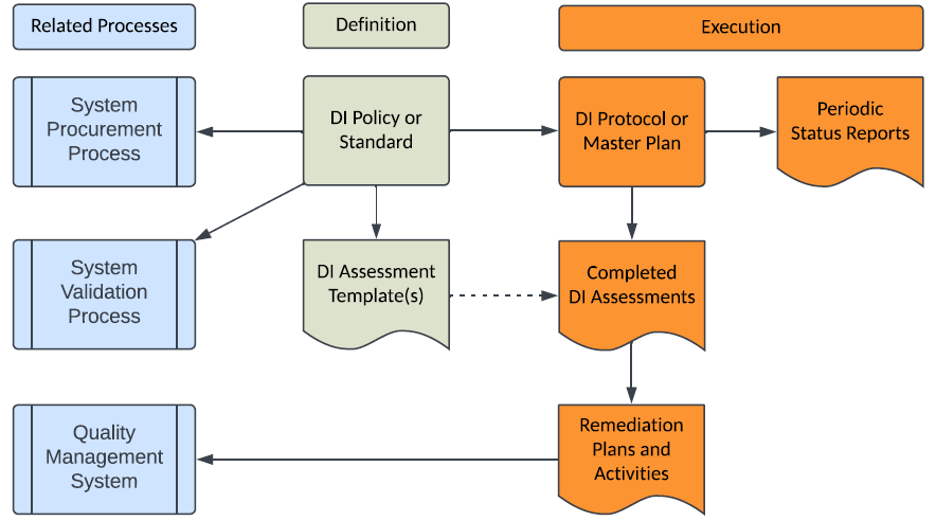
1. The Data Integrity Policy or Standard (depending on your QMS hierarchy) is the starting point for a Data Integrity Program and defines your company’s requirements for the integrity of GxP data, both in paper and electronic formats. This policy or standard should define the data integrity requirements for GxP data throughout its lifecycle, from its creation to its final disposition or destruction. This policy or standard should cover the following:
a) Compliance to ALCOA + Principles that state GxP data should be (A) Attributable, (L) Legible, (C) Contemporaneous, (O) Original, (A) Accurate and the “+” portion also includes Complete, Consistent, Enduring and Available. Data Integrity guidance from the FDA, MHRA and numerous industry organizations consistently cite ALCOA to define the necessary attributes of GxP data. Further details on ALCOA are found in the FDA and MHRA guidance listed in the Additional Information on Data Integrity section at the end of this article.
b) Program requirements:
- Ensuring management support, prioritization, and program funding
- Defining management and staff responsibilities
- Providing ongoing Data Integrity training
c) Core Data Integrity requirements:
- System administration, system access, audit trails, data backup
- Secure electronic records, electronic signatures
- Hosted GxP systems and GxP data, supplier compliance
- Network and system data security, management of system controlling computers
- Consistent and synchronized time sources and clocks
- Data transfers and migrations
- Spreadsheets
d) Special Case Data Integrity requirements:
- Manual (paper-based) processes and systems
- Programmable logic controller (PLC) based systems
- Legacy processes and systems
- Analytical assays
e) Requirements for establishing and maintaining a system’s validated state:
- Computer System Validation (CSV) or Computers System Assurance (CSA)
- System periodic reviews, system access reviews, system audit trail reviews
- Change control
2. Data Integrity Assessment Template(s) will establish a consistent assessment approach for existing and new GxP processes or systems to identify any Data Integrity compliance gaps that require remediation.
3. Data Integrity Protocol or Master Plan will establish a risk-based process and specific steps to implement the requirements defined in the Data Integrity Policy or Standard. This protocol or master plan should remain open until all existing GxP processes and systems are assessed and remediated, and then closed thereafter. This document should be both pre and post approved by your company’s Management Team and Quality Assurance to ensure their knowledge and concurrence with the approach prior to execution and its subsequent completion.
Priority Categories (e.g., High, Medium, Low) based on the impact that data integrity gaps may have upon human health and safety, product integrity or product release, client operations or any other criteria that is meaningful to your company, should be defined with their rational in this document. The Priority Categories establish a structured, defensible, and risk-based approach for assessing and remediating your company’s GXP processes and systems.
The following high-level activities should be defined in this document:
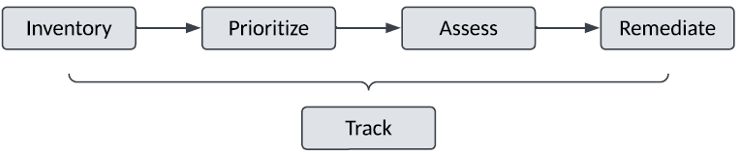
a) Establish and document an Inventory of existing GxP processes and systems:
- This inventory should be a snapshot in time of the existing GxP processes and systems and should not be updated with subsequently implemented (new) GxP processes and systems.
- The Data Integrity assessment of new GxP processes and systems should be managed by the system procurement and system validation processes (see the Impact to Related Process section below).
b) Prioritize the Inventory of existing GxP Processes and Systems for data integrity assessment and remediation by:
- Assigning each GxP process and system a Priority Category and further prioritize within each category as needed.
- Recording the list of GxP processes and systems within each Priority Category as an addendum to your Data Integrity Protocol or Master Plan or as a stand-alone document.
c) Assess each GxP process and system for Data Integrity compliance gaps:
- For existing systems, perform the assessments in priority order as defined by the Priority Categories.
- For new systems, perform an assessment as part of the procurement and validation processes to avoid implementing systems with Data Integrity gaps.
d) Remediate any assessed Data Integrity gaps:
- Data Integrity compliance gaps resulting from the assessment of existing systems should be remediated under change control.
- Data Integrity compliance gaps resulting from the assessment of a new system should be remediated and tested during system implementation and validation.
e) Track the status and completion of the above activities to:
- Report status on the execution of the Data Integrity Protocol or Master Plan.
- Identify compliance gap trends which may have potential common remediation solutions.
4. Completed Data Integrity Assessments document any compliance gaps for the GxP process or system assessed.
5. Remediation Plan or Activities can be documented as part of the Data Integrity Assessment Template, a stand-alone document and/or recorded as CAPAs within the Quality Management System (QMS) to facilitate tracking and trending.
6. Periodic Data Integrity Status Reports to demonstrate progress on the activities listed in the Data Integrity Protocol or Master Plan to the management team, internal auditors, clients and regulatory authorities.
Impact to Related Processes
The Data Integrity Policy or Standard may impact related, existing processes that may require update:
- The System Procurement process should be updated to utilize a high-level checklist to verify that any systems under consideration can be implemented in compliance with applicable Data Integrity, 21 CFR Part 11 and EudraLex Vol 4 Annex 11 requirements.
- The System Validation process (Computer System Validation or Computer Software Assurance) should be updated to include and verify applicable Data Integrity, 21 CFR Part 11 and EudraLex Vol 4 Annex 11 requirements to ensure new and updated systems support Data Integrity.
- The Quality Management System (QMS) should be used to record and manage remediation activities to completion as CAPAs. All system changes resulting from remediation activities should be performed under Change Control.
Conclusion
A Data Integrity programs are not only necessary to establish a defensible position with regulatory authorities and clients, but more importantly, they are necessary to ensure the integrity of drug development, clinical trials, drug manufacturing and ultimately, trial subject and patient safety.
This is the first in a series of articles on Data Integrity in a GxP environment. This article highlighted the need for, structure and execution of a Data Integrity Program. Future articles will describe Data Integrity requirements in more detail as well as the assessment and remediation processes.
Additional Information on Data Integrity
- FDA 21 CFR Part 11: Electronic Records; Electronic Signatures (Mar 1997)
- FDA Part 11, Electronic Records; Electronic Signatures – Scope and Application (Aug 2003)
- FDA Data Integrity and Compliance with CGMP: Guidance for Industry (Apr 2016)
- FDA Data Integrity and Compliance with Drug CGMP: Questions and Answers Guidance for Industry (Dec 2018)
- MHRA GXP Data Integrity Guidance and Definitions (Mar 2018)
- EudraLex Volume 4 Good Manufacturing Guidelines, Annex 11: Computerised Systems (Jan 2011)
- ISPE GAMP 5: A risk-based approach to Compliant GxP Computerized Systems (2008)
- ISPE GAMP; Records and Data Integrity Guide (Mar 2017)
- PDA Technical Report No. 80, Data Integrity Management System for Pharmaceutical Laboratories (2018)
- PIC/S Draft Guidance: Good Practices for Data Management and Integrity in Regulated GXP/GDP Environments (Nov 2018)
Kevin DeLeon is a Principal Consultant in CREO’s Cybersecurity and Compliance practice and is an expert in IT Quality and Compliance for regulated environments. The CREO Cybersecurity and Compliance practice has deep expertise in GxP systems implementation and validation, SDLC processes and oversight, QMS and related policies, procedures and supporting activities, Data Integrity, Part 11/Annex 11, Lab Buildouts, Cybersecurity, and program operationalization.
 Kevin DeLeon | February 20, 2023
Kevin DeLeon | February 20, 2023


